The digital revolution has brought incredible convenience to our lives and opened doors for new forms of harassment. Among these emerging threats, call bombing stands out as one of the most disruptive and anxiety-inducing attacks. When someone uses a Call Bomber Protection against your phone number, your device becomes unusable as hundreds or thousands of automated calls flood your line within minutes.
Call bomber attacks have become increasingly sophisticated and accessible. These malicious tools can send up to 1000 calls per hour to a single target, making your phone completely unusable for legitimate purposes. The psychological impact can be severe, causing stress, anxiety, and disrupting both personal and professional communication. Whether the attack stems from a prank gone wrong, personal revenge, or targeted harassment, the results are equally devastating for victims.
This article will explore comprehensive call bomber protection strategies, examine the latest security apps and technologies available in 2025, and provide practical steps to prevent and stop call bombing incidents.
Understanding Call Bomber Protection: The Modern Digital Threat
Call Bomber Protection represents a sophisticated form of digital harassment where automated systems flood a target phone number with continuous calls. These attacks utilize specialized software or online platforms that can generate massive volumes of calls simultaneously. The technology behind these attacks has evolved significantly, with platforms offering features like custom caller ID spoofing, scheduled attacks, and personalized harassment messages.
The mechanics involve automated systems that bypass traditional telecom security measures using VoIP technology, making calls appear to originate from different numbers or locations. Some platforms allow attackers to mask their identity altogether, making it extremely difficult to trace the source.
The impact extends beyond mere annoyance. Victims report feeling helpless and violated as their primary communication device becomes unusable. Emergency calls cannot be made or received during active attacks, potentially creating dangerous situations. Business professionals lose critical client communications, students miss academic opportunities, and families cannot reach each other during crucial moments.
Essential Call Bomber Protection Strategies for 2025
Modern call bomber protection requires a multi-layered approach combining technological solutions with behavioral precautions. The most effective protection strategies integrate advanced AI-powered detection systems with traditional call blocking methods.
Advanced AI-Powered Protection Systems
The latest call bomber protection technologies employ artificial intelligence to detect and block mass calling patterns in real-time. These systems analyze incoming call behavior, identifying suspicious patterns that indicate automated attacks. Military-grade AI protection systems now achieve 99.9% accuracy in detecting call bombing attempts, blocking attacks within milliseconds.
Innovative protection systems learn from user behavior, allowing important calls while blocking harassment attempts. These technologies create comprehensive threat profiles, track attack patterns, and automatically block threatening numbers with Work-Level Protection Solutions
Major telecom providers now offer enhanced spam protection services integrated directly into their networks. Carriers like Jio, Airtel, and Vi provide built-in spam filtering through their mobile apps. The SHAKEN/STIR framework, implemented across major networks, provides caller ID authentication that helps prevent number spoofing, a common tactic used in call bombing.
Top Call Bomber Protection Apps: 2025 Analysis
1. Truecaller: The Global Community Shield

Truecaller remains the most comprehensive call bomber protection solution, leveraging a database of over 450 million users worldwide. The app automatically identifies and blocks known spam numbers, with its community-driven approach ensuring real-time updates on new threats.
Advanced features include automated top spammer blocking, with daily updates to spam lists ensuring protection against newly identified threats. Premium users benefit from automatic spam list updates, while free users can manually update their protection databases. Truecaller’s fraud detection extends to SMS messages, providing comprehensive protection against text-based attacks.
2. Hiya: Real-Time Threat Detection
Hiya specializes in real-time spam and scam detection, utilizing carrier-grade technology that processes billions of calls monthly. The app’s AI-driven identification system precisely recognizes business, personal, international, and unknown calls. Advanced features include secure visual voicemail with multi-language transcription and proactive scam blocking.
3. Call Control: Advanced Customization
Call Control offers three distinct call blocking modes, allowing users to customize how spam calls are handled. The app’s CommunityIQ feature helps users discover which numbers other community members have marked as spam. The personal blocklist and allowlist functionality provides granular control over call management.
Should I Answer?: Offline Protection
Should I Answer? Provides unique offline protection capabilities, maintaining spam databases that function without internet connectivity. This feature proves invaluable for users who travel frequently or have limited data connectivity. The app allows users to choose between blocking incoming or outgoing calls from overseas, hidden, and unknown numbers.
Built-in Phone Call Bomber Protection Features
1. Android Protection Systems
Android devices offer robust built-in spam call protection through the Google Phone app. The “Filter spam calls” feature blocks identified spam calls from ringing, though filtered calls still appear in call history for review. Samsung Galaxy phones feature Smart Call technology that filters unwanted calls and provides enhanced caller ID information.
2. iPhone Security Features
iPhone users can activate “Silence Unknown Callers” through Settings, automatically sending calls from unknown numbers to voicemail. The iPhone’s integration with third-party call blocking apps enhances protection while maintaining system stability.
Emergency Response and Recovery Procedures
1. Immediate Response Actions
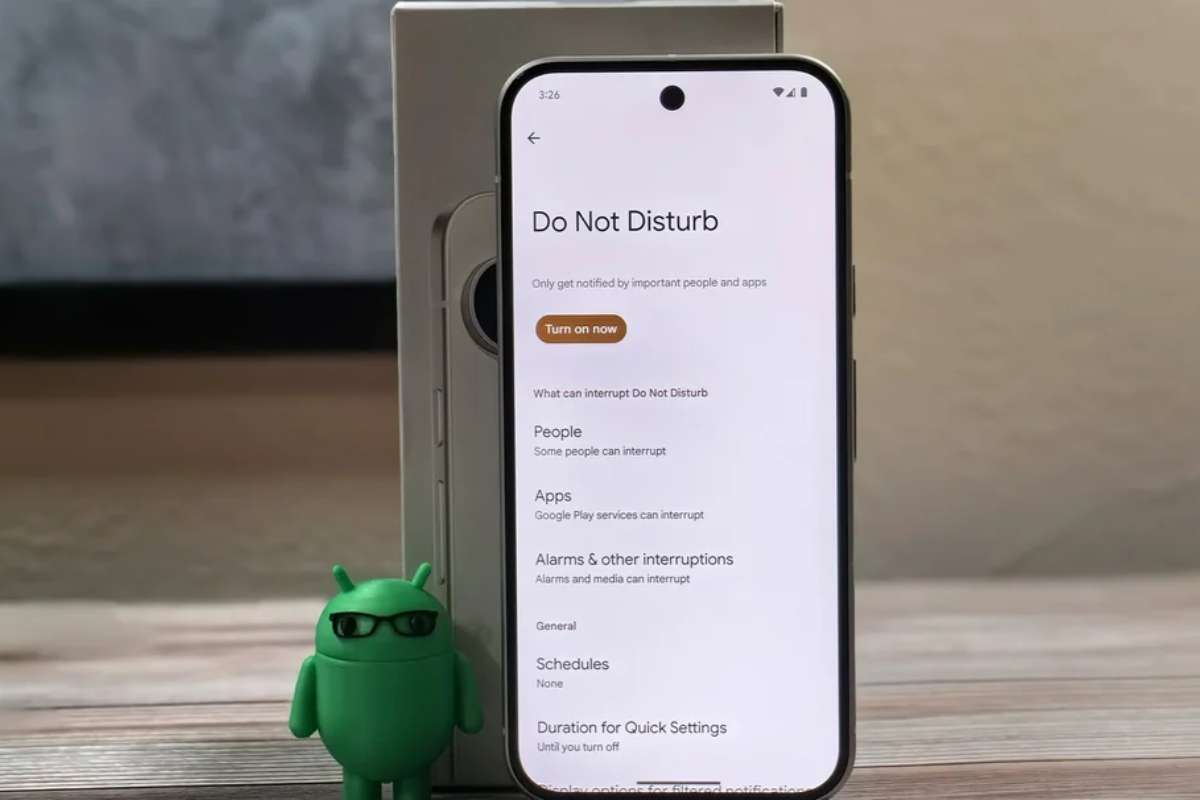
When facing an active call bomber attack, immediate action can minimize damage and restore communication capabilities. The first step involves activating “Do Not Disturb” mode, allowing only contacts in your address book to reach you. This provides instant relief from the barrage of calls while maintaining access for essential communications.
Most call bombing platforms provide “stop” mechanisms to halt ongoing attacks. Visiting the suspected attack website and using their stop function can end the bombing within 2-5 minutes, though some queued calls may continue for up to 10 minutes.
2. Protection List Registration
Many call bombing platforms maintain protection lists that prevent numbers from being targeted. Adding your number to these databases provides permanent protection against future attacks from those specific platforms. However, protection on one platform does not guarantee security from other services.
3. Legal Framework and Cybercrime Reporting
Call bombing constitutes a form of cyberstalking and cyberharassment, falling under various national and international cybercrime laws. The legal classification as cybercrime enables law enforcement agencies to pursue criminal charges against perpetrators.
Victims should document all aspects of attacks, including timestamps, caller IDs, and platform sources when known. The National Cyber Crime Reporting Portal accepts reports of call bombing attacks, with specialized procedures for harassment incidents. Telecom providers often offer specialized support for customers experiencing these attacks.
Prevention Best Practices
1. Digital Hygiene Protocols

Preventing call bomber attacks requires careful management of personal information sharing. Avoid posting phone numbers on public platforms, social media profiles, or untrusted websites. Be cautious when providing phone numbers for online services, contests, or applications that may not have robust privacy protections.
2. Network Security Measures
Register for Do Not Disturb (DND) services through your telecommunications provider to reduce exposure to marketing and spam calls. In India, sending an SMS to 1909 or calling the same number activates comprehensive DND protection. Enable built-in spam protection features on your device and keep security software updated.
Also Read :- Virtualization Technologies: Transforming IT Landscapes
3. Proactive Monitoring
Regularly monitor your phone number’s exposure across online platforms and services. Consider using dedicated business lines or virtual numbers for professional communications, keeping personal numbers private and secure. This compartmentalization limits exposure and makes it easier to manage security incidents.
4. Recovery and Long-Term Security
Conduct a comprehensive security review after experiencing a call bomber attack to identify how your number was obtained and targeted. Monitor for secondary attacks or attempts to use other attack vectors like SMS bombing or social media harassment.
Establish alternative emergency communication channels, including backup phone numbers, messaging apps, and email systems. Regularly review and update call blocking settings across all protection apps and services. Stay informed about new call bombing techniques and protection technologies through cybersecurity news sources.
Conclusion
Call bomber protection in 2025 requires a comprehensive approach combining advanced technology, legal awareness, and proactive security practices. The threat continues to evolve, but with proper preparation and the right tools, individuals can maintain secure and reliable communication channels despite these digital harassment campaigns. The key lies in implementing multiple layers of protection, staying informed about emerging threats, and taking swift action when attacks occur.
Also Read :- SMS Bomber Protection 2025: How to Protect Your Phone from Message Floods









